Spam – A look into the scourge of the internet
Today I want to touch a bit on the subject of spamming. The scourge of the internet!
Spammers have forever been a plague to the world wide web ever since the first years of its existence. Yet, were we to go deeper into who they are, we would categories spammers into three distinctive groups:
- Automated
- Semi-automated
- Human-based
Automated spam bots render similarities with Search engine indexing bots, as they crawl the internet looking for email addresses and/or different forms on websites.
Once they find an email, they immediately store it into a database for a later use by a human scammer or; usually and especially nowadays, the entire process from collection to delivery is 100% automated.
Thanks to modern spam filters and CAPTCHAs, the fight is on. But, like it or not, spammers as well keep evolving thus remaining a serious threat.
Just the previous day, Google announced that they are rolling out the new version of their ReCAPTCHA. What makes it better and smarter? Well, it does not even need human interaction in order to tell the difference between a bot and a human. The moment a robot is detected, a control question pops up asking the bot to solve it. Conversely, in the case of humans, this process doesn’t take place. Pretty cool, right?
These are some of the most common spam scams:
Phishing
 Typically carried out by email or instant messaging on social media, through phishing, the user will often be directed to a fake website whose look and feel are almost identical to any legitimate one. However here, as you are entering your details on the form you are provided with, your login information will be stored with them. In this simple way, your account will be hijacked and they will have gotten all your information as fast as you say cheese.
Typically carried out by email or instant messaging on social media, through phishing, the user will often be directed to a fake website whose look and feel are almost identical to any legitimate one. However here, as you are entering your details on the form you are provided with, your login information will be stored with them. In this simple way, your account will be hijacked and they will have gotten all your information as fast as you say cheese.
The best way to minimize the risk of a hijack by phishing is to activate a 2 step verification process on your accounts. Most services nowadays support this, so no need to worry about the rest. Once your 2 step verification process has been activated, a code will be sent on your phone or via an authorization app, like Authy. With the code entered on your phone, even if they still have your login information, it will not be enough to get access.
Nigerian emails

These ones are commonly called the “Nigerian emails” and often consist of a human part that sends out an email to a huge amount of recipients. Well, how come they are still so popular among hijackers, despite their notoriety as obvious scams? Think about it: though most of us just delete such an email as we can tell it’s a scam, all they need is ONE or TWO individuals out of hundred thousands recipients to fall into the trap and consider it legit.
Different variations linked to this type of scam are called anything from the Nigerian Letter to the Nigerian scam, Nigerian bank scam, or Nigerian money offer. And yeah! Expect these scammers to go the extra mile, adding to the letters The Nigerian Senate emblem just to prove a point.
If you’re looking for a laugh, you can visit and read the 419 eater site, they are “scamming the scammer” through social engineering and post the email threads on the site.
Global spam volume as percentage of total e-mail traffic from 2007 to 2015
How big is the actual spam mail problem and what percentage of all the emails sent every year do spams represent? Well, Statista has the answer:
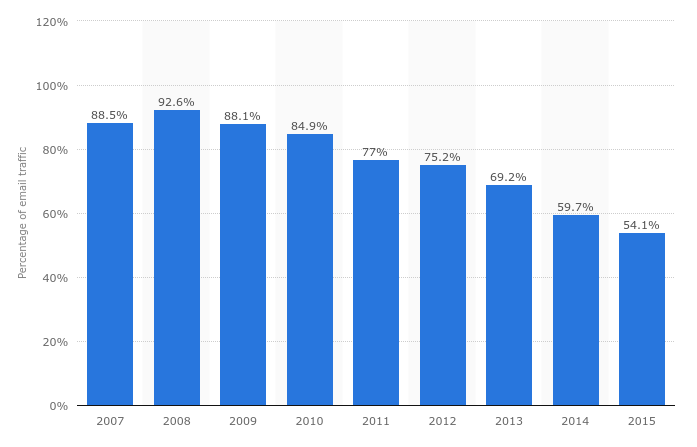 Source: Statista.com
Source: Statista.com
As you examine the graph above, you can see that in 2008, the 92.6% (!!) of total global emails sent on the internet were spam. Therefore, only 7.4% of all emails sent that year were legit normal emails. Since then, the number has been going down year by year. Mostly thanks to international razzias against botnet server parks.
Well, that’s all for today, have a fantastic weekend everybody!
